December 18, 2023
A Night of Horror: Security Incident Analysis of Ledger Connect Kit

On December 14, 2023, according to the Beosin EagleEye Threat Intelligence Platform, a large number of decentralized applications suffered asset theft due to maliciously implanted libraries in Ledger, resulting in hackers profiting over $600,000. Beosin team promptly conducted an analysis of the incident, and the findings are as follows.
Introduction to Connect Kit
Connect Kit is a Javascript library by Ledger that enables users to connect their Ledger devices to third-party DApps. Library link: https://www.npmjs.com/package/@ledgerhq/connect-kit
Vulnerability Analysis
The incident occurred because a former Ledger employee fell victim to a phishing attack, and Ledger did not revoke the employee’s code access permissions. Consequently, the attacker gained access to their NPMJS account. Subsequently, the attacker released a malicious version of Ledger Connect Kit (affected versions: 1.1.5, 1.1.6, and 1.1.7).
Attack Process
Four months ago, the attacker released the malicious version 1.1.5 of Ledger Connect Kit, followed by versions 1.1.6 and 1.1.7 two months ago. These versions were distributed via CDN, utilizing malicious code to transfer users’ funds to specified hacker wallet addresses.
Fund Tracking
The hacker’s fund address (0x658729879fca881d9526480b82ae00efc54b5c2d) has been marked as Ledger Exploiter by EagleEye, and users can monitor it in real-time on the EagleEye website:

https://eagleeye.space/address/0x658729879fca881d9526480b82ae00efc54b5c2d. The attack involved multiple public chains, with funds transferred in Ethereum, BNB Chain, Arbitrum, Base, Fantom, and other networks, resulting in profits exceeding $600,000.
According to Beosin trace queries, as of the publication date, a portion of the stolen funds on Ethereum was sent to the phishing address Fake_Phishing268838 (0x1b9f9964a073401a8bc24f64491516970bb84e47), while the rest remains in the attacker’s address (due to the numerous token types, only partial information is displayed in the images).
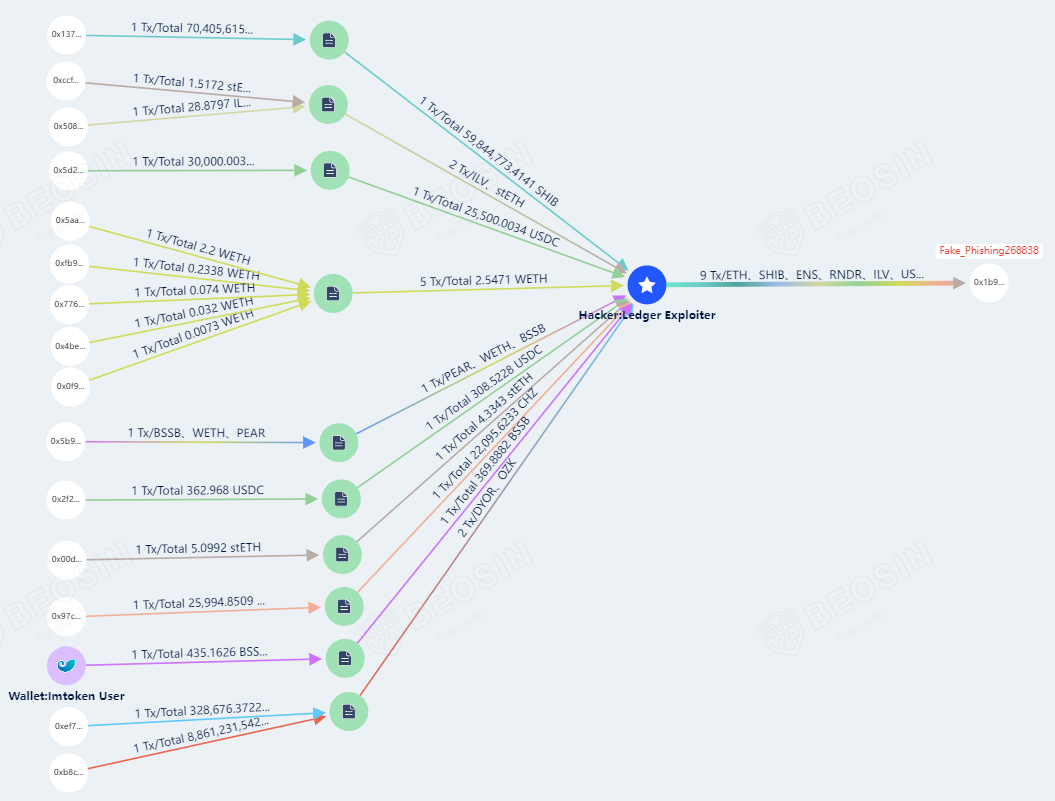
All stolen funds on the BSC chain are currently stored in the attacker’s address.

This incident involved a large number of users being compromised on various public chains, with only Ethereum and BSC theft details presented here.
Security Recommendations
This incident underscores the importance of supply chain security. In Web3 security, supply chain security is often overlooked by developers and security teams, enabling hackers to implant malicious code at various points in the software supply chain, leading to large-scale attacks on user information and digital assets.
Beosin recommends the following measures to prevent such security incidents:
- Conduct security reviews and verification when selecting and using third-party software or components. Understand the third party’s security standards and practices to ensure the software is free from tampering or malicious code.
- Adopt secure development practices, including the use of secure coding standards, code reviews, vulnerability scans, and security testing, to ensure the software remains secure throughout the development process.
- Promptly apply security updates and patches released by software vendors to fix known vulnerabilities and defects. Keep software up to date to minimize the risk of attacks.
- Implement a multi-layered security defense strategy, including network security, endpoint security, and data security. Use measures such as intrusion detection systems, endpoint security software, and data encryption to enhance the overall security of the software supply chain.
- Establish monitoring and response mechanisms to promptly detect abnormal activities and potential supply chain attacks. Take appropriate response measures, such as isolating infected code repositories, timely fixing vulnerabilities, and restoring data.
- Provide employee training and awareness programs to enable them to identify social engineering and supply chain attacks and take appropriate preventive measures, such as being vigilant against phishing emails and refraining from downloading attachments indiscriminately. Update developer team’s permissions transparently and clearly during code handovers.
Contact
If you need any blockchain security services, welcome to contact us:
Related Project
Related Project Secure Score
Guess you like

Analyzing the Viral Spread of xPet in the Web3 Space: A Security Perspective on the Recent Buzz
December 12, 2023

Event Recap | How Does User Security and Regulatory Compliance Affect the Future Development of Web3?
December 19, 2023

DePIN Spotlight: Assessing Development, Ecosystem, and Challenges
December 22, 2023

2023 Global Web3 Security Statistics & AML Analysis
December 28, 2023
